Welcome to TechUnder5, where tech meets simplicity—fast. In today’s post, we’re diving into one of the most important shifts in modern IT infrastructure — understanding the evolution from traditional Active Directory to Microsoft Entra ID. Whether you’re an IT professional, developer, or just cloud-curious, knowing how Microsoft’s identity solutions have evolved is critical for securing cloud-based environments and managing users in the modern workplace.
What is Traditional Active Directory (AD)?
Let’s start with Active Directory (AD) which is Microsoft’s original on-premises identity and access management (IAM) solution, introduced with Windows 2000 Server. It is widely used in enterprise environments for:
- Centralized authentication and authorization
- Managing users, groups, and computers in a domain
- Group Policy configuration
- Integration with legacy and on-premises applications
It relies on:
- Kerberos and NTLM (NT LAN Manager) for authentication
- LDAP (Lightweight Directory Access Protocol) for directory queries
- A domain controller (DC) structure
While powerful, traditional AD is not designed for cloud-native applications or remote access without complex add-ons like ADFS (Active Directory Federation Services).
Why Active Directory Doesn’t Work Well in the Cloud
Traditional AD was built for a world where users, devices, and resources all lived inside the same physical network — typically within a corporate firewall. But the modern workplace has changed dramatically:
- Users are mobile, accessing resources from laptops, phones, and remote locations.
- Apps are in the cloud, not on a local file server.
- Devices are diverse, including personal smartphones and unmanaged laptops.
- Security perimeters have blurred, making perimeter-based access control obsolete.
Because of these shifts, traditional AD faces major limitations in a cloud-first world:
- It requires VPNs or ADFS (Active Directory Federation Services) to extend access securely outside the corporate network.
- It is tightly coupled to Windows environments, limiting cross-platform usability.
- It doesn’t support modern authentication standards like OAuth2 (Open Authorization 2.0) or SAML (Security Assertion Markup Language) natively.
- Managing identities across multiple SaaS (Software as a Service) platforms (e.g., Salesforce, Zoom) is cumbersome.
To address these challenges, Microsoft introduced Azure AD (now Microsoft Entra ID) as a cloud-native identity platform built for flexibility, scalability, and secure access to cloud applications.
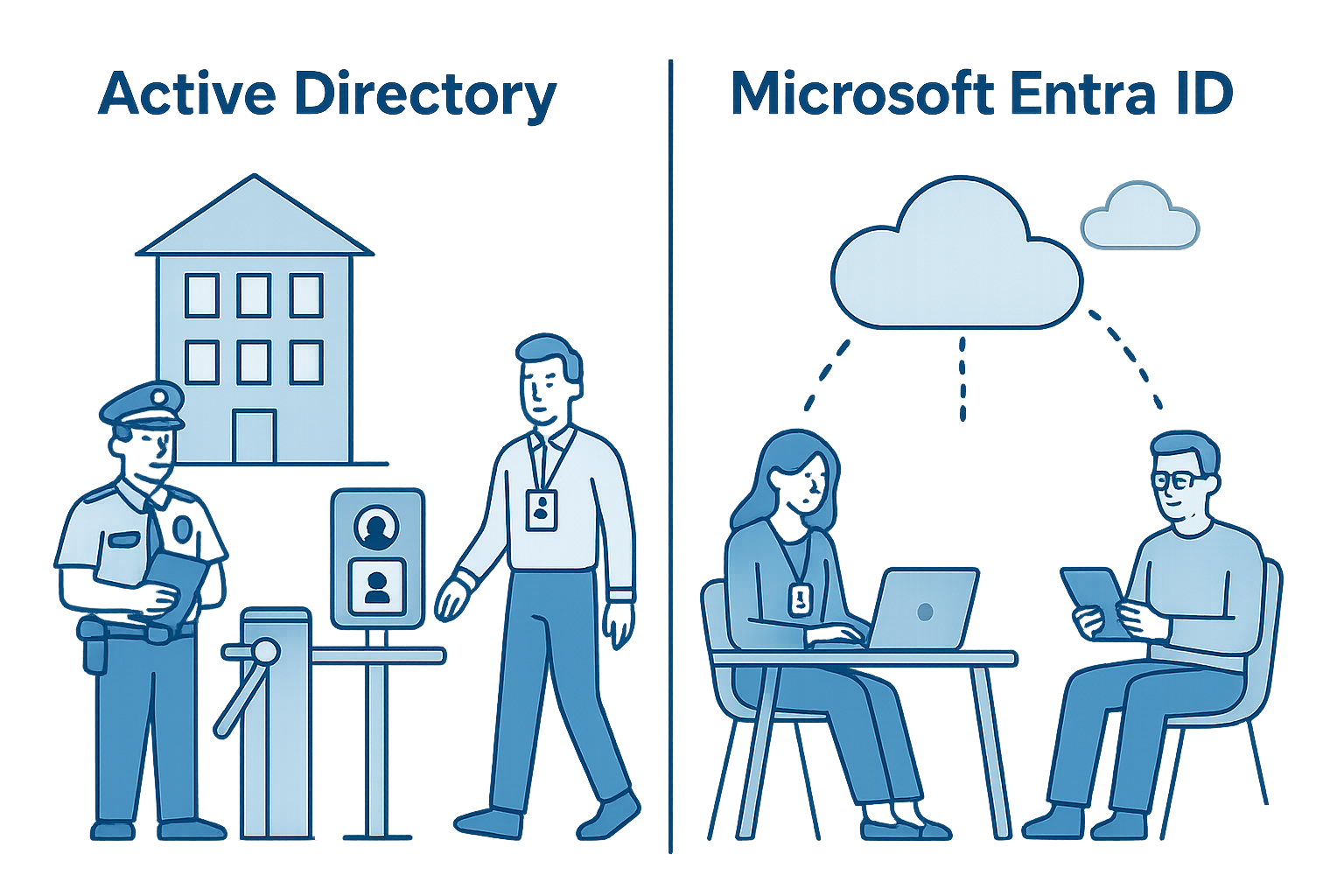
🏛️ Real-World Analogy:
Think of Traditional Active Directory like the security and management system of a corporate office building in the early 2000s:
- Employees must come into the building to access files or tools.
- A front desk security guard (Domain Controller) checks ID badges before allowing entry.
- Access to rooms and equipment is granted based on physical keys or badges (user credentials).
- Policies like “you must wear a badge at all times” are enforced via internal rules (Group Policy).
Everything works well as long as people are physically in the office, but it gets complicated when employees work remotely or when you try to connect external tools without retrofitting the whole system.
What is Azure AD (now Microsoft Entra ID)?
Think of Azure AD / Microsoft Entra ID as the “Active Directory of the cloud” — purpose-built for modern, internet-connected environments. While it shares the core goal of managing identities and access, it differs in architecture, protocols, and capabilities to better serve cloud-first organizations.
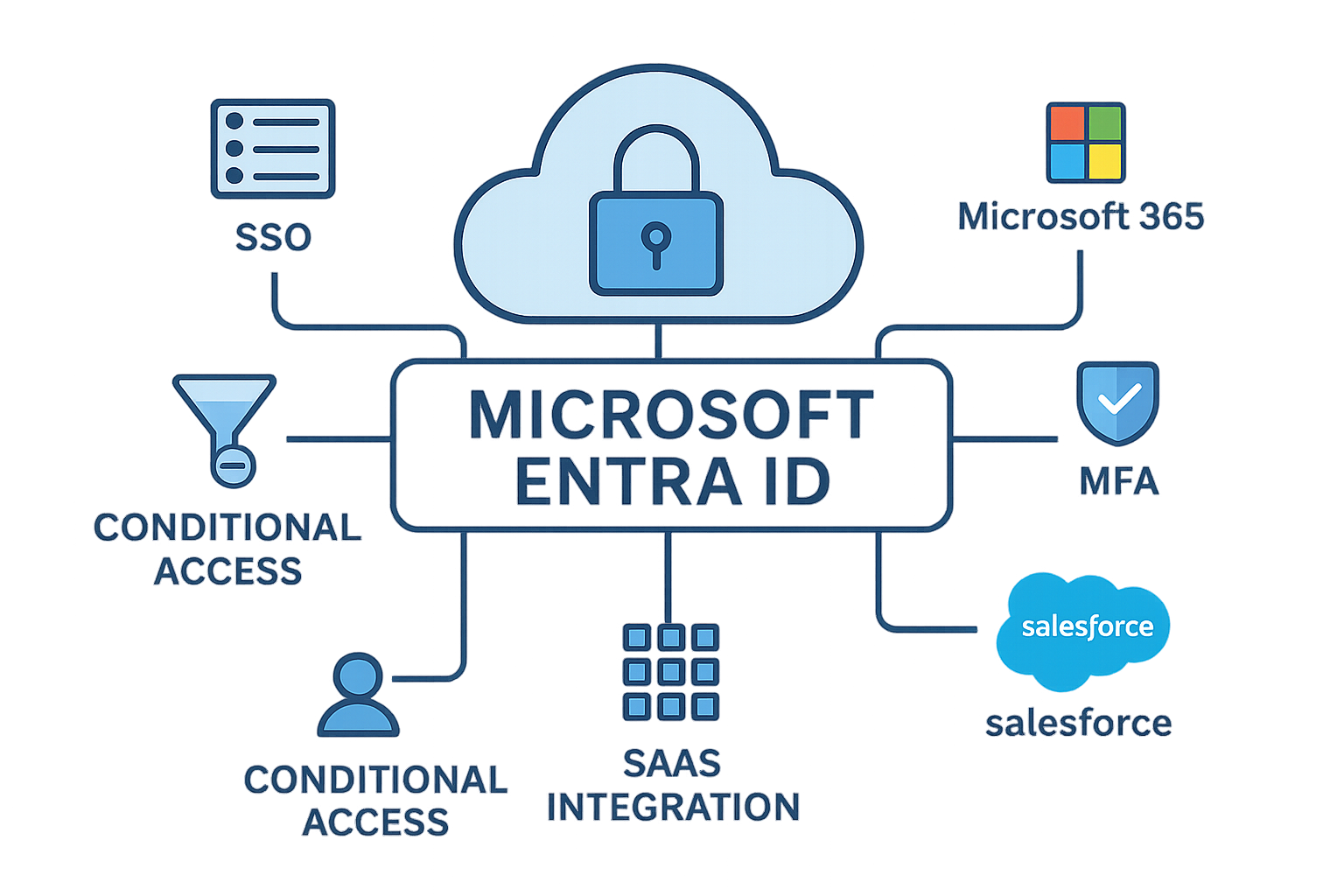
Azure Active Directory (Azure AD) was Microsoft’s cloud-based IAM service built for modern applications and services. It enabled:
- Single Sign-On (SSO) to cloud apps (e.g., Microsoft 365, Salesforce)
- Integration with SaaS (Software as a Service) platforms (e.g., Salesforce, Zoom)
- Multi-factor authentication (MFA)
- Conditional access and identity governance
- Seamless login across devices and platforms
In July 2023, Microsoft rebranded Azure AD as Microsoft Entra ID. This was part of a broader push under the “Entra” umbrella to unify identity, access, and security products. Key Point: Entra ID is not a new product, but a new name for Azure AD.
Has Anything Changed with Entra ID?
No. Only the name has changed.
- All features from Azure AD are still available
- Your settings, licenses, and integrations are unaffected
- Microsoft documentation now uses the name Microsoft Entra ID
Comparison Chart: AD vs Azure AD vs Microsoft Entra ID
| Feature / Capability | Traditional AD (On-Prem) | Microsoft Entra ID (Current Name) |
|---|---|---|
| Deployment Location | On-premises | Cloud-based |
| Authentication Protocols | Kerberos, NTLM (NT LAN Manager) | OAuth2 (Open Authorization 2.0), OpenID Connect, SAML (Security Assertion Markup Language) |
| Domain Join | Yes | Azure AD Join / Hybrid Join |
| Supports Group Policy | Yes | No |
| Single Sign-On (SSO) for Cloud | No | Yes |
| MFA Support | Limited | Yes |
| Conditional Access | No | Yes |
| SaaS App Integration | No | Yes |
| Identity Governance | Basic | Advanced |
| Current Branding | Active Directory | Microsoft Entra ID(Formerly Azure AD) |
Final Thoughts
If you’re using Microsoft 365, chances are you’re already using Microsoft Entra ID (formerly Azure AD). Understanding the rebrand helps clarify the future direction of Microsoft’s identity services.
- AD is for legacy, on-prem environments
- Entra ID (formerly Azure AD) is the future of identity in the cloud
Stay updated, and you’ll be well-prepared to manage identity in modern hybrid and cloud environments.
